System Architecture Overview
As a solution architect, I designed and implemented a comprehensive Software Over-the-Air (SOTA) update system for a state-of-the-art vehicle cockpit controller. This complex system orchestrates seamless software updates across multiple domains with varying operating systems while maintaining robust security, reliability, and regulatory compliance.
The core of the architecture is a heterogeneous cockpit controller with a System-on-Chip (SoC) design that includes a dedicated safety island. This architecture provides clear separation of concerns:
- Safety Island: Runs Classic AUTOSAR for safety-critical functions
- Main SoC: Operates under a hypervisor managing multiple virtual machines:
- QNX for real-time operations
- Android for user interface and applications
- Linux container within the Android VM for specialized services
The system extends beyond the cockpit controller to include:
- A vehicle processor running Classic AUTOSAR
- An audio DSP chip running FreeRTOS
- 8 display modules with their own firmware
- A radio tuner module
All components communicate via an Ethernet switch, creating a distributed network that requires precise coordination for updates. Each component features a dual-bank memory architecture to ensure reliability during the update process.
Software Update Manager (SUM) Architecture
At the heart of my design is a centralized Software Update Manager (SUM) that orchestrates the entire update process. This component-based architecture provides several advantages:
1. Unified Interface: SUM exposes a consistent SOMEIP service interface that can be used by any update client, whether OTA or wired (UDS DoIP)
2. State Management: Maintains consistent states across all update targets
3. Scalability: The architecture can be deployed across multiple ECUs in the vehicle
4. Reliability: Handles interruptions gracefully with pause/resume capabilities
The stateful SUM component guides targets through a well-defined update lifecycle:
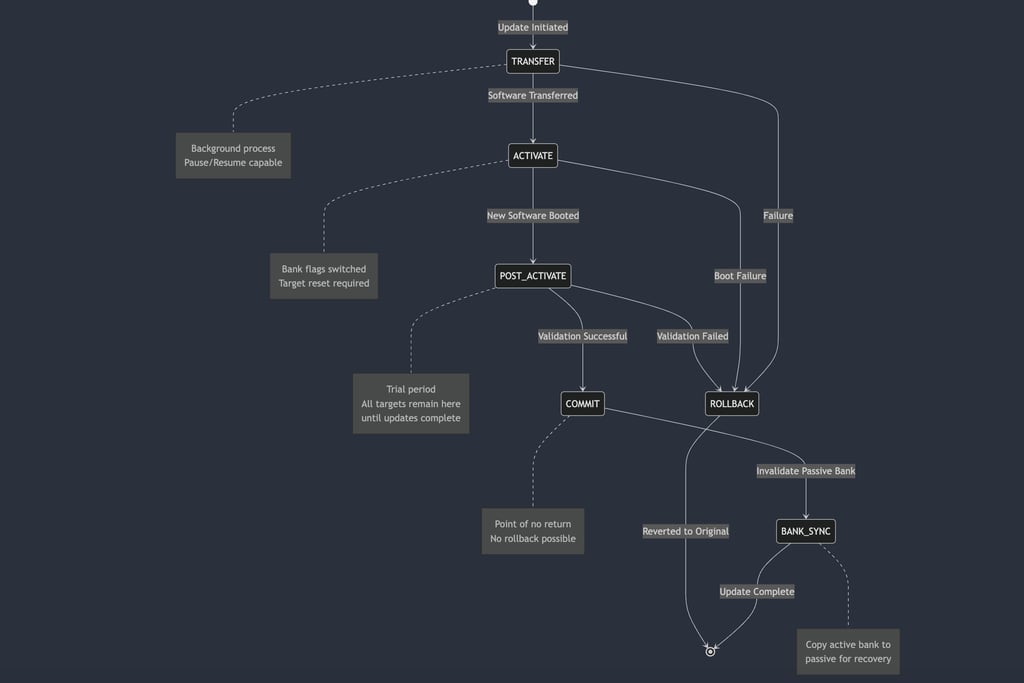
Update Lifecycle States
The update process flows through the following carefully designed states:
TRANSFER
During this state, new software is installed into the passive bank of the target component while the vehicle remains fully operational. This background process has been optimized for low-priority execution to prevent any impact on vehicle functionality. The architecture implements pause and resume capabilities to handle vehicle shutdown scenarios, ensuring the transfer can continue seamlessly when the vehicle is restarted.
ACTIVATE
Once transfer is complete, the system prepares to switch to the new software. This critical state manages the switching of bank flags so that the target boots from the previously passive bank (containing the new software). The architecture typically requires a controlled reset of the target component during this phase.
POST-ACTIVATE
After activation, the new software enters a trial period to verify proper functionality. This safety window allows for observation before final commitment. A key architectural decision was to have all targets remain in post-activation until every component's transfer and activation is complete, ensuring system-wide consistency.
COMMIT
The commit state represents the point of no return, where the system accepts the new software as permanent. The passive bank is invalidated, preventing any further rollback to the previous version. This state is only entered after comprehensive validation during the post-activation phase.
BANK SYNCHRONIZATION
As a sub-state of commit, bank synchronization replicates the active bank's software to the passive bank. This creates a safety backup for recovery scenarios where the active bank might become corrupted, exemplifying the architecture's focus on resilience.
> Note: Rollback capabilities exist from any state except commit. Once committed, the system cannot revert to the previous software version, making bank synchronization essential for future recovery scenarios.
Component Interactions
The architecture implements a clear separation of concerns through a layered approach:
1. Software Update Manager (SUM): Central orchestrator maintaining state
2. Installer Libraries: Stateless adaptors for each component type, abstracting hardware-specific details from SUM
3. Update Agents: Embedded in each target component, implementing local state management and edge-case handling
This design provides both centralized control and distributed resilience. If SUM fails during an update, the agent can execute automatic rollback procedures, preventing bricked components.
Update Package Architecture
The solution uses a sophisticated update package structure—a compressed file containing:
- Software images for each target component
- Metadata describing components, update order, and activation sequences
- Dependency information to manage complex interdependencies between components
This package architecture enables intelligent deployment planning, particularly critical when managing updates across components with different operating systems and boot requirements.
Security and Compliance
Security was architected into every aspect of the system:
- Package Signing: All update packages are cryptographically signed and verified by SUM before installation
- Image Signing: Individual software images are signed to enable secure boot across all components
- Anti-rollback Protection: Prevents downgrade attacks by enforcing version progression
- SHA-256 Verification: SUM verifies component integrity using cryptographic hashes
The hashing mechanism serves dual purposes:
1. Traceability: Each hash maps to a software part number recognized by the campaign management team
2. Regulatory Compliance: The system meets UNECE R156 requirements for software update traceability
Update Methods
The architecture supports multiple update delivery mechanisms:
1. Wired Updates: Using UDS DoIP (Diagnostic over IP) for service center updates
2. Over-the-Air Updates: For remote deployment through cellular or Wi-Fi connectivity
Both methods leverage the same SUM interface, maintaining consistency while accommodating different deployment scenarios.
Software Over-the-Air Updates for Vehicle Cockpit Controllers
Balu Pillai
Automotive Solutions Architect
London, United kingdom
contact@balupillai.com
+447438432741
© 2025. All rights reserved.
